Configure Rule Engine
The Rule Engine allows customization of how Anti-DDoS accesses are handled (response headers, TTL, etc.), providing greater control over web application behavior through rules.
Each rule can have up to 5 conditions and 3 actions. Each Anti-DDoS endpoint can have up to 15 rules (including the default rule).
- Actions that can be set on the default rule.
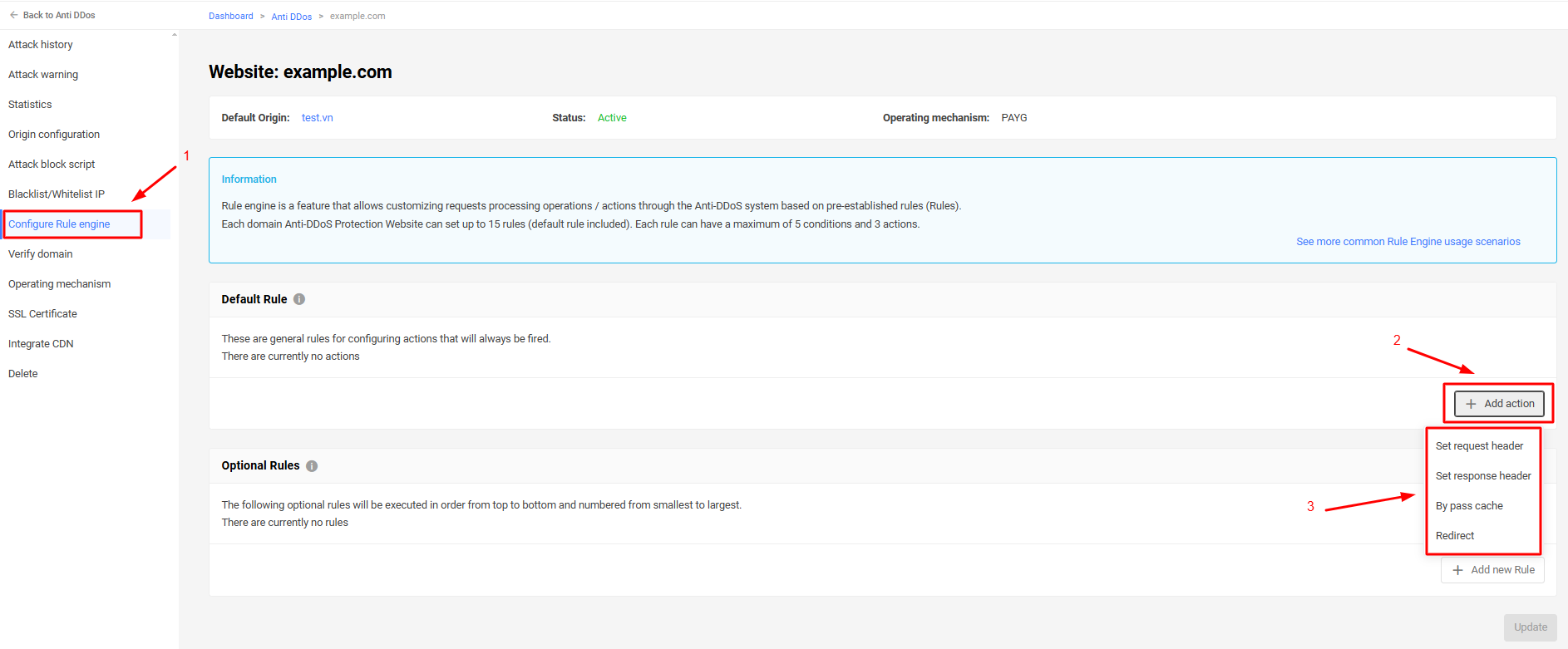
- Set request header: Action to configure request headers.
- Set response header: Action to configure response headers.
- Bypass cache: Action to bypass cache (True/False).
- Redirect: Action to redirect on message(301/302).
Some common configuration cases
Configure CORS
Customers can perform operations to change the default rules in the “Configure rules engine” task according to their usage needs.
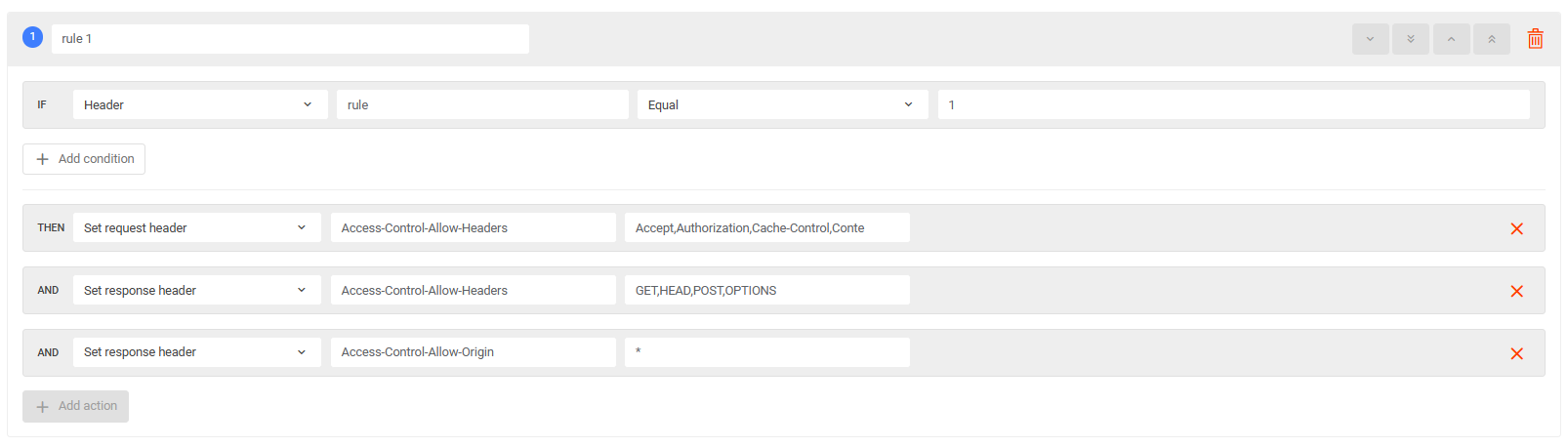
| Set request header | Access-Control-Allow-Headers | Accept,Authorization,Cache-Control,Content-Length,Content-Type,DNT,If-Modified-Since,Keep-Alive,Key,máy chủ gốc,Range,User-Agent,X-Requested-With |
|---|---|---|
| Set response header | Access-Control-allow-Methods | GET, HEAD, POST, OPTIONS |
| Set response header | Access-Control-Allow-root server | * |
Configuration output:
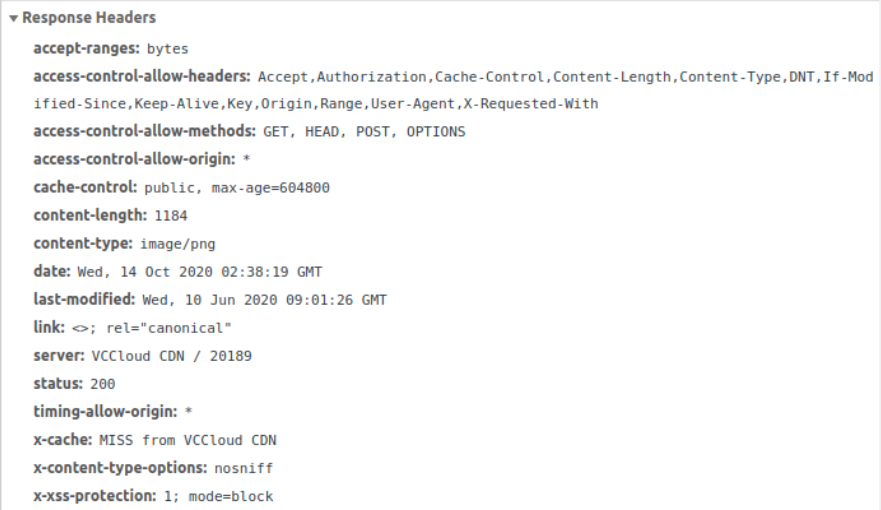
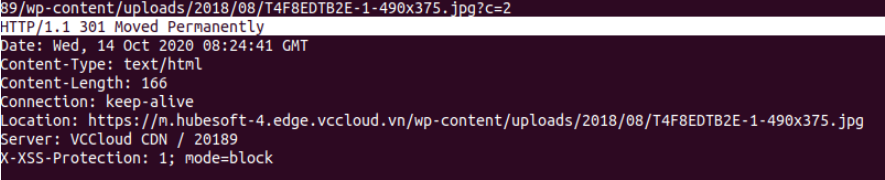
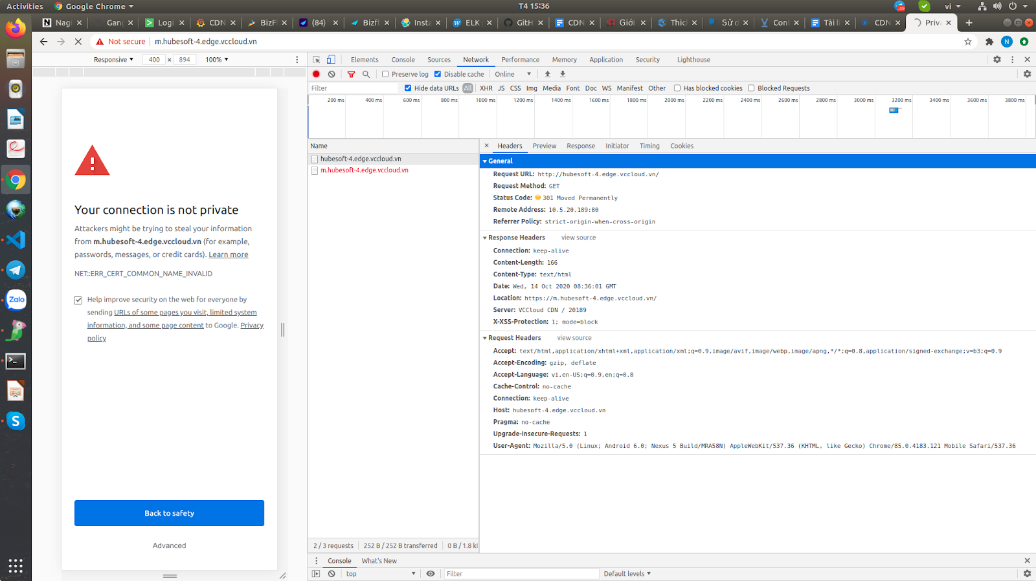
Redirect from http => https
- Requests from mobile/computer devices accessing example.com will be redirected to m.example.com/example.com upon receiving a notification.
- Requests from mobile/computer devices accessing will be redirected to http/https.
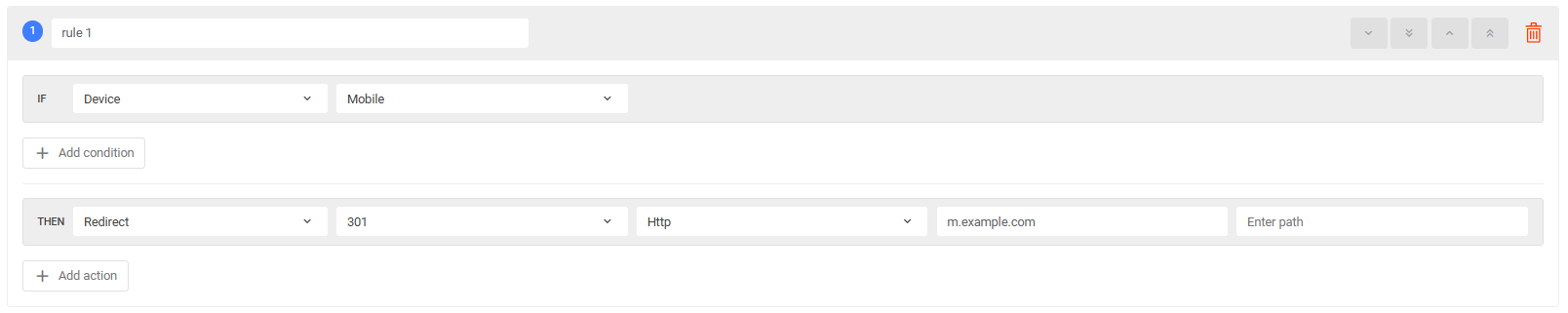
Configuration output when adding rules:
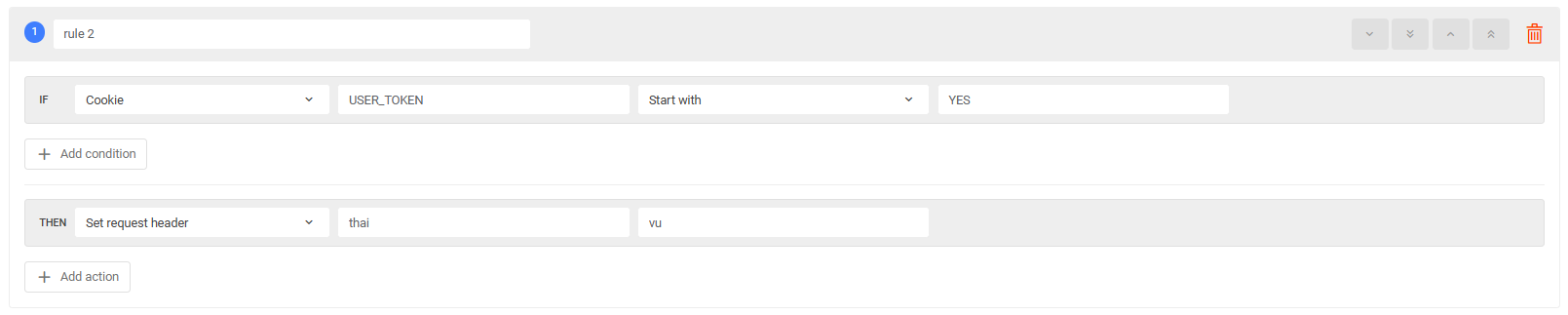
Redirect request by Cookie
Requests with the cookie beta=1 accessing example.com will be redirected to beta.example.com.
Configuration output when adding rules:
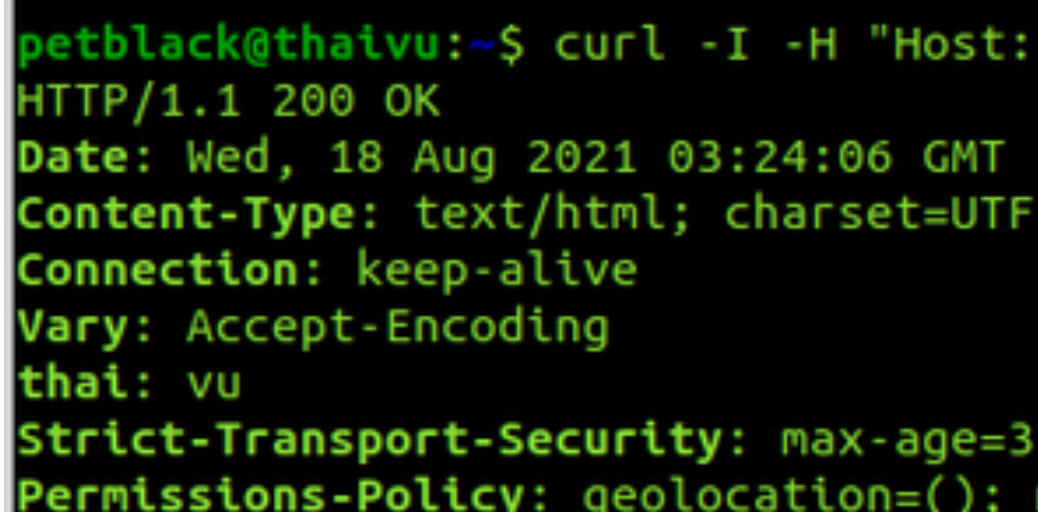
Redirect requests based on path
Operator can be use:
- start with
- not start with
- end with
- not end with
- contain
- not contain
- equal
- not equal
- less than
- not less than
- greater than
- not greater than
- Requests to /path are served from a customized group override on the origin server.
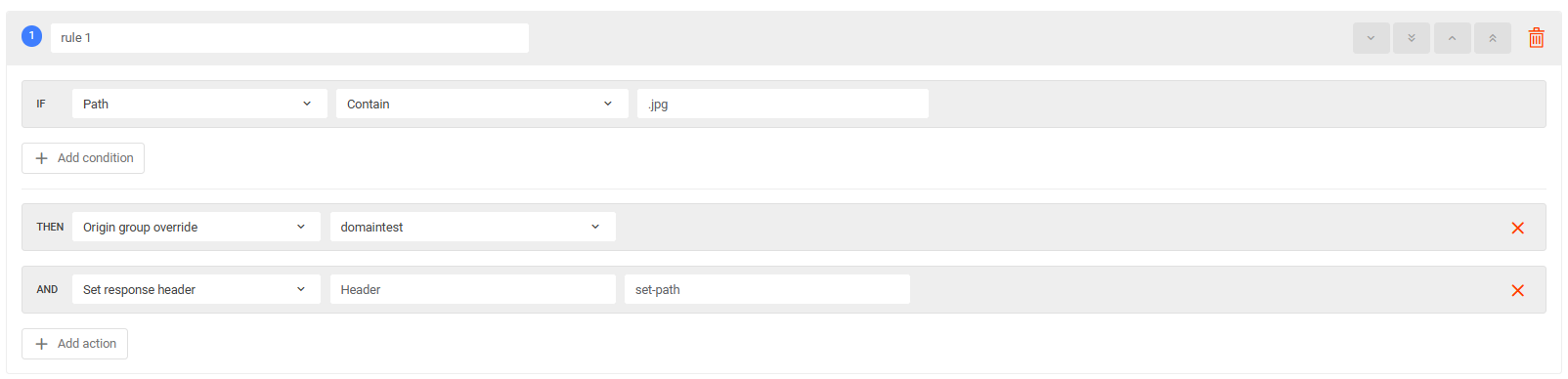
In this case, a header will be added to requests containing .jpg